데모 애플리케이션 배포
- Empire의 mediabot pod가 Empire의 git 저장소 관리를 위해 GitHub에 접근해야 하는 간단한 시나리오를 사용.
- pod는 다른 외부 서비스에 접근할 수 없어야 한다.
# hubble ui 에 pod name 표기를 위해 app labels 추가 >> 빼고 배포해보고 차이점을 확인해보자.
cat << EOF > dns-sw-app.yaml
apiVersion: v1
kind: Pod
metadata:
name: mediabot
labels:
org: empire
class: mediabot
app: mediabot
spec:
containers:
- name: mediabot
image: quay.io/cilium/json-mock:v1.3.8@sha256:5aad04835eda9025fe4561ad31be77fd55309af8158ca8663a72f6abb78c2603
EOFkubectl apply -f dns-sw-app.yaml
kubectl wait pod/mediabot --for=condition=Ready
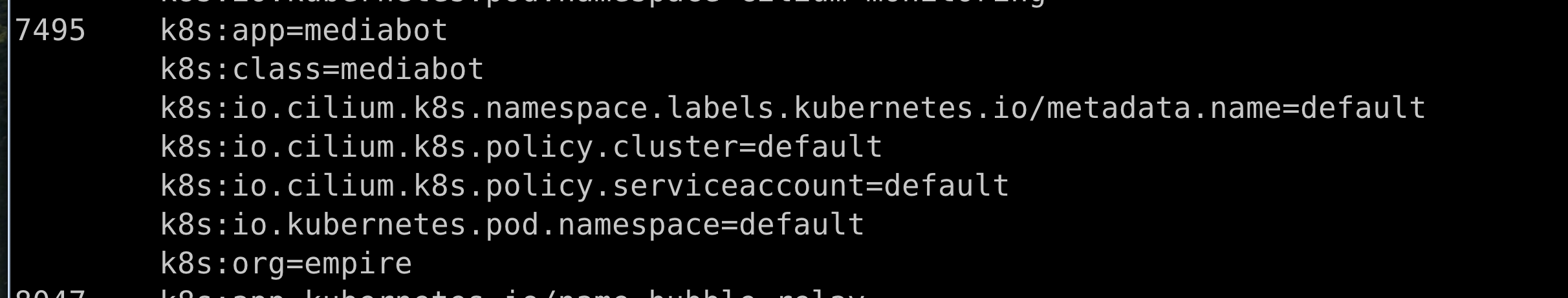
kubectl exec -it -n kube-system ds/cilium -- cilium identity list
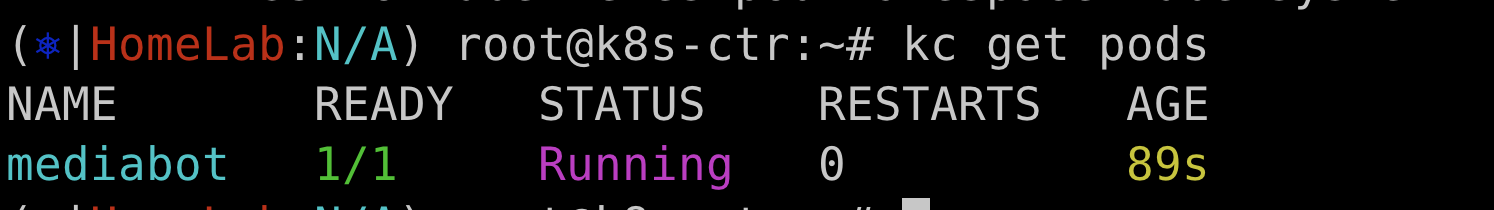
kubectl get pods
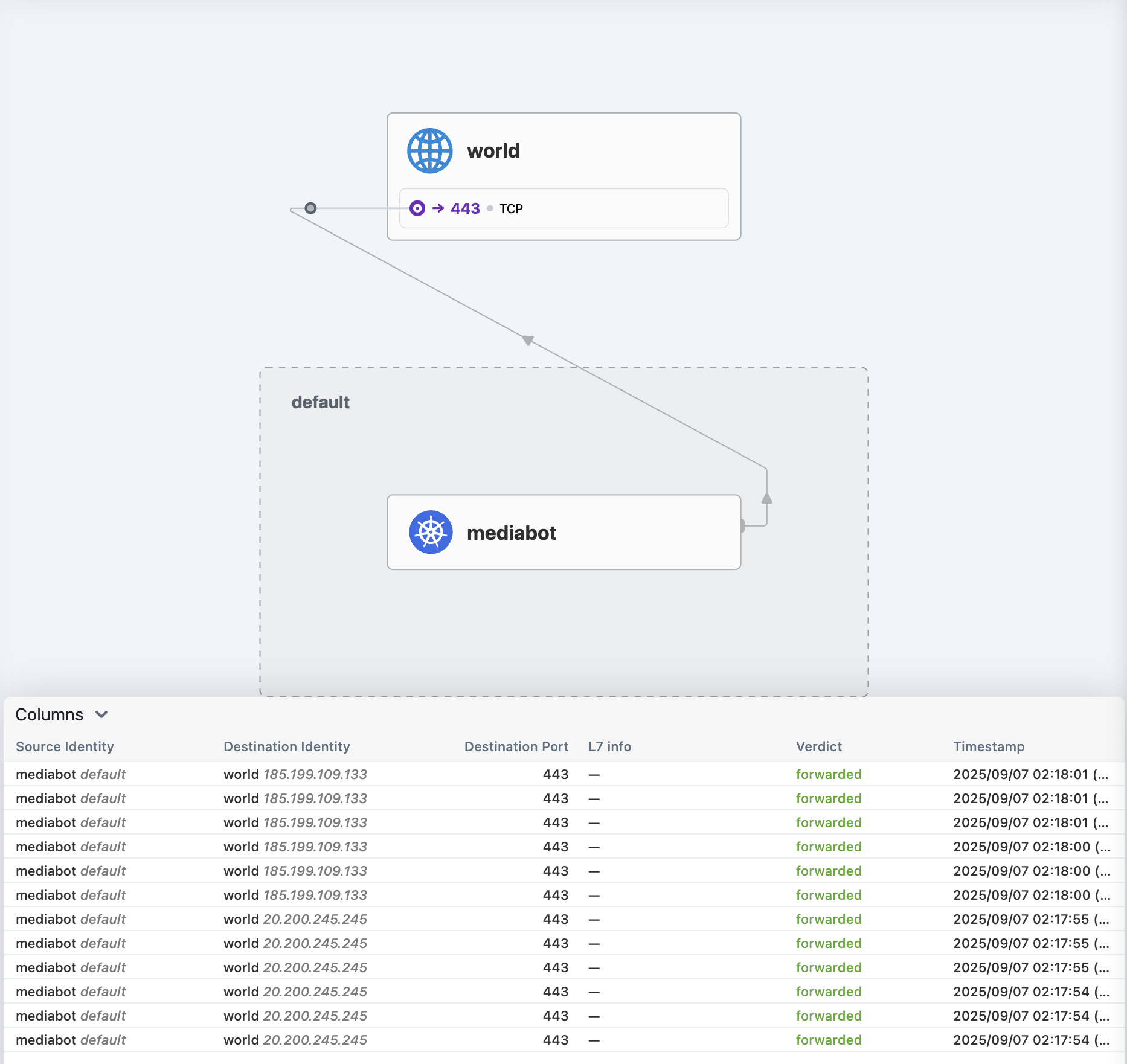
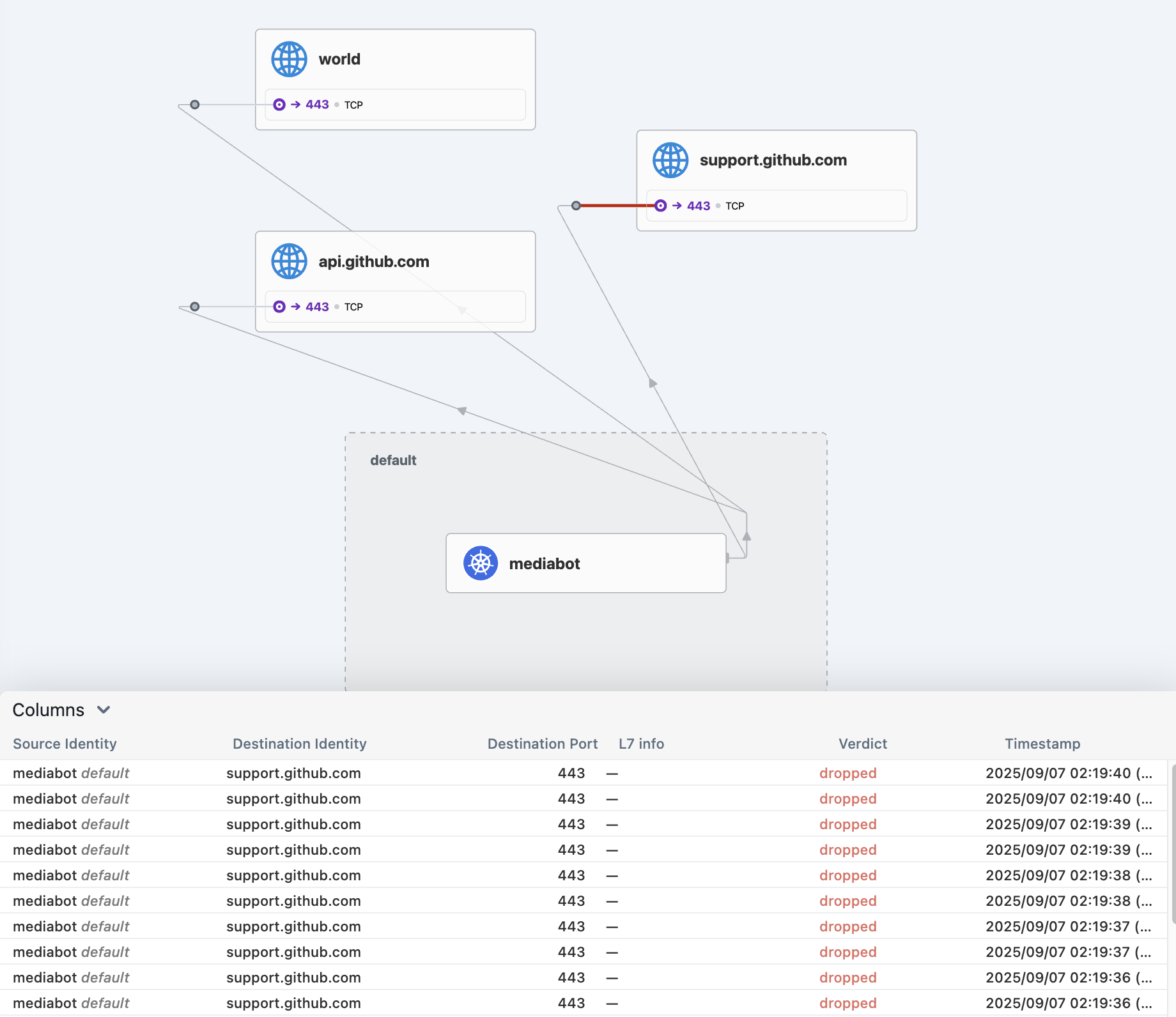
# 외부 통신 확인 : hubble ui 에서 확인
kubectl exec mediabot -- curl -I -s https://api.github.com | head -1
kubectl exec mediabot -- curl -I -s --max-time 5 https://support.github.com | head -1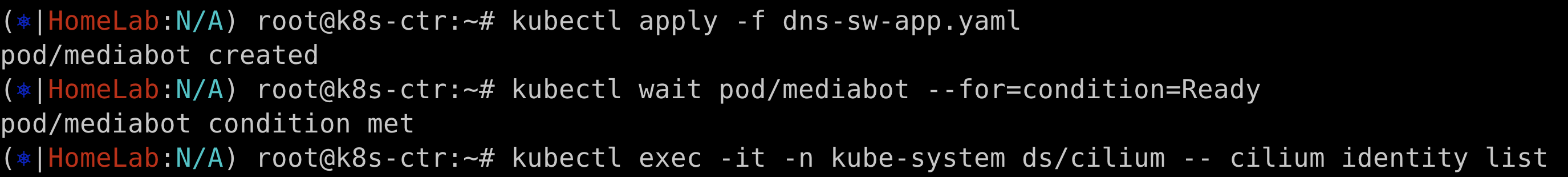
DNS Engress 정책 적용 1
cat << EOF | kubectl apply -f -
apiVersion: "cilium.io/v2"
kind: CiliumNetworkPolicy
metadata:
name: "fqdn"
spec:
endpointSelector:
matchLabels:
org: empire
class: mediabot
egress:
- toFQDNs:
- matchName: "api.github.com"
- toEndpoints:
- matchLabels:
"k8s:io.kubernetes.pod.namespace": kube-system
"k8s:k8s-app": kube-dns
toPorts:
- ports:
- port: "53"
protocol: ANY
rules:
dns:
- matchPattern: "*"
EOF
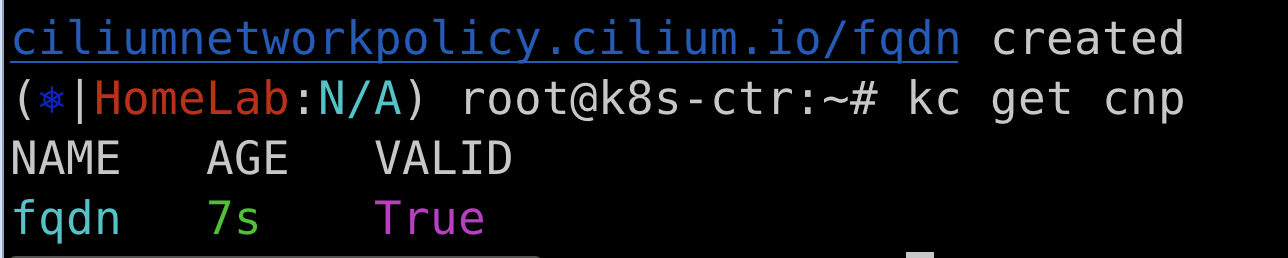
# 확인
kubectl get cnp
NAME AGE VALID
fqdn 4s True
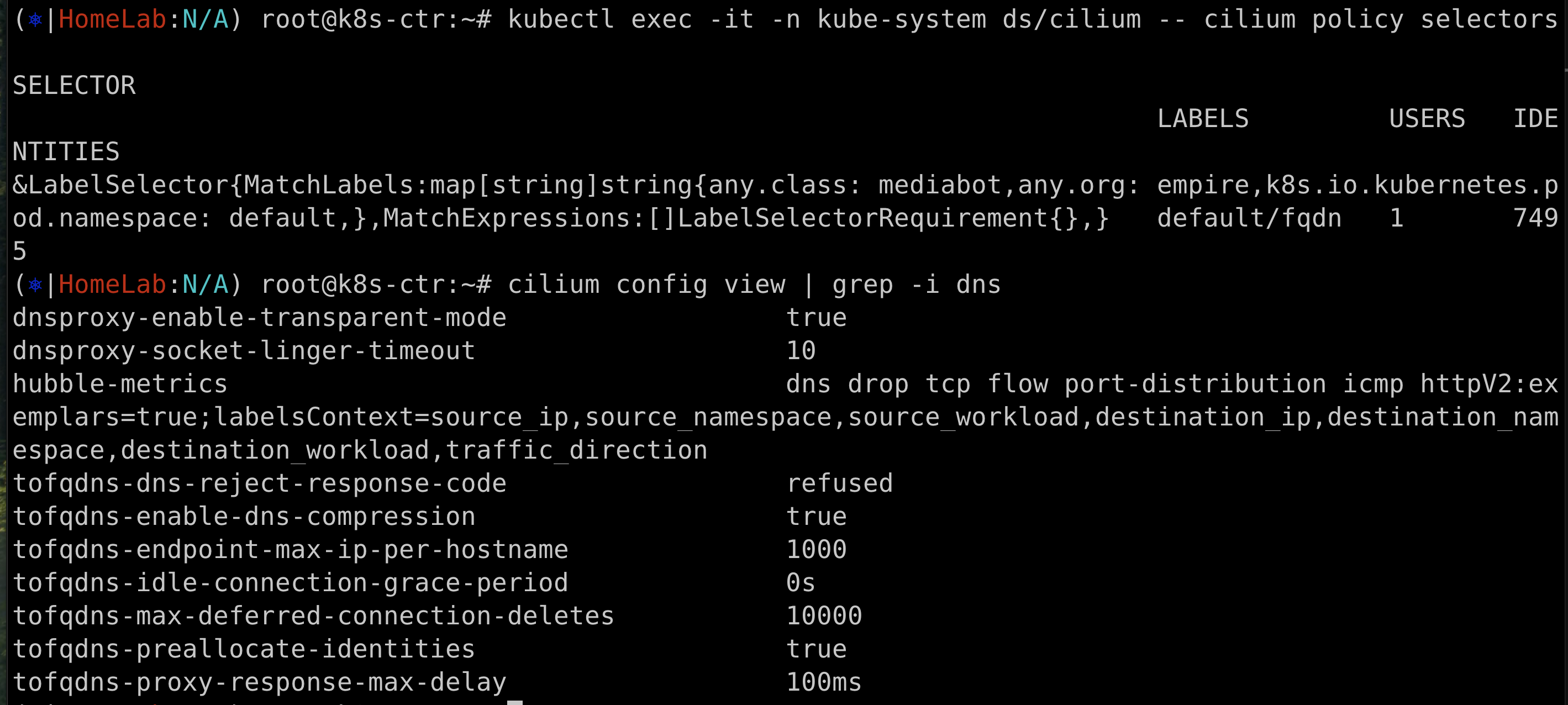
kubectl exec -it -n kube-system ds/cilium -- cilium policy selectors
SELECTOR LABELS USERS IDENTITIES
&LabelSelector{MatchLabels:map[string]string{any.class: mediabot,any.org: empire,k8s.io.kubernetes.pod.namespace: default,},MatchExpressions:[]LabelSelectorRequirement{},} default/fqdn 1 5190
cilium config view | grep -i dns
dnsproxy-enable-transparent-mode true
dnsproxy-socket-linger-timeout 10
hubble-metrics dns drop tcp flow port-distribution icmp httpV2:exemplars=true;labelsContext=source_ip,source_namespace,source_workload,destination_ip,destination_namespace,destination_workload,traffic_direction
tofqdns-dns-reject-response-code refused
tofqdns-enable-dns-compression true
tofqdns-endpoint-max-ip-per-hostname 1000
tofqdns-idle-connection-grace-period 0s
tofqdns-max-deferred-connection-deletes 10000
tofqdns-preallocate-identities true
tofqdns-proxy-response-max-delay 100ms
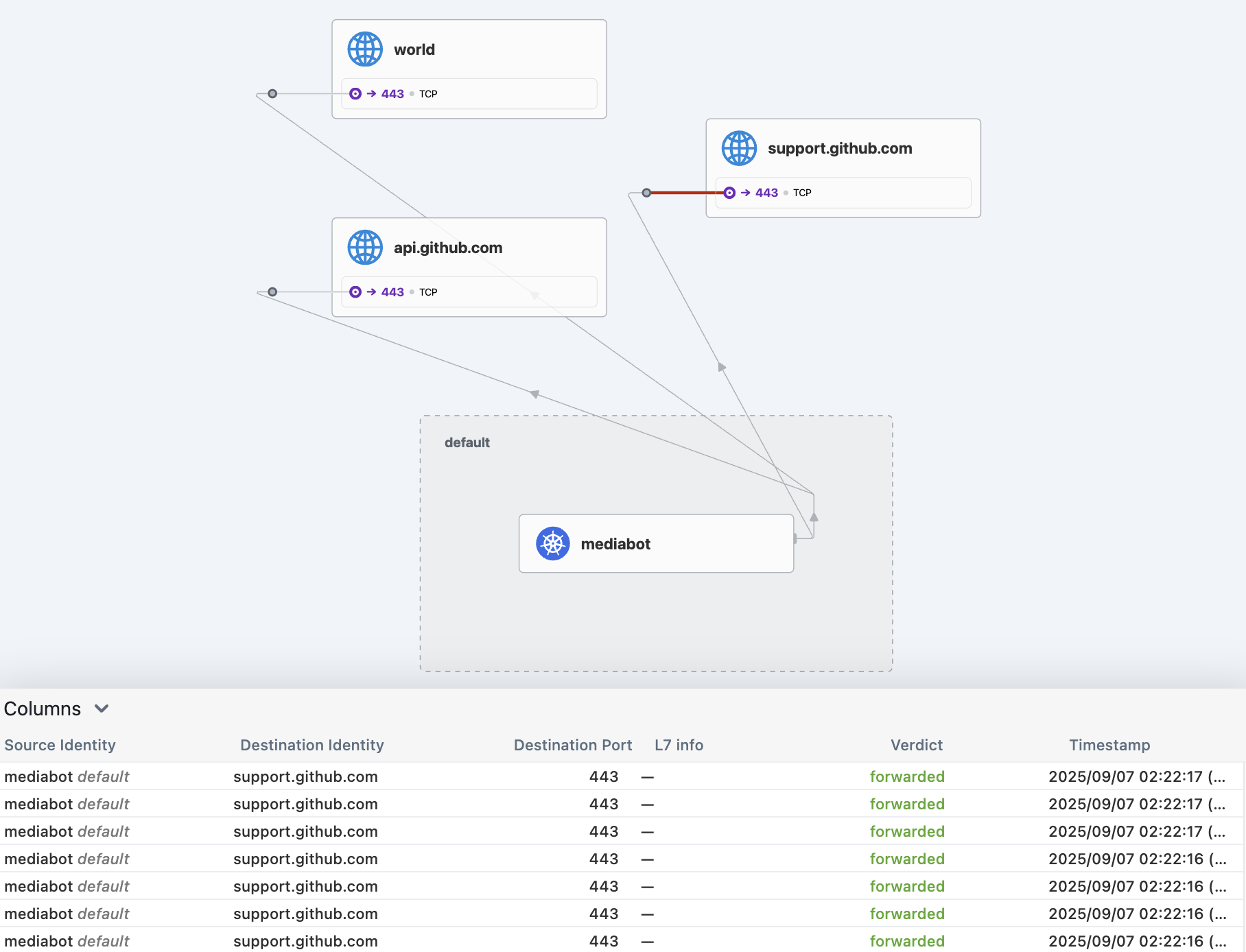
# 외부 통신 확인 : hubble ui 에서 확인
kubectl exec mediabot -- curl -I -s https://api.github.com | head -1
kubectl exec mediabot -- curl -I -s --max-time 5 https://support.github.com | head -1
# cilium-agent 내에 go 로 구현된 lightweight proxy 가 DNS 쿼리/응답 감시와 캐싱 처리 : 기본 30초?
cilium hubble port-forward&
hubble observe --pod mediabot
Aug 31 03:59:53.209: default/mediabot:47883 (ID:5190) <- kube-system/coredns-674b8bbfcf-p6pbn:53 (ID:1363) dns-response proxy FORWARDED (DNS Answer "20.200.245.245" TTL: 30 (Proxy api.github.com. A))
...
Aug 31 03:59:53.212: default/mediabot:38212 (ID:5190) -> api.github.com:443 (ID:16777217) policy-verdict:L3-Only EGRESS ALLOWED (TCP Flags: SYN)
...
# (옵션) coredns 로그로 직접 확인해보기
k9s -> configmap (coredns) : log 추가
## 로깅 활성화
kubectl logs -n kube-system -l k8s-app=kube-dns -f
## 호출
kubectl exec mediabot -- curl -I -s https://api.github.com | head -1
kubectl exec mediabot -- curl -I -s https://api.github.com | head -1
hubble observe --pod mediabot
## cilium 파드 이름
export CILIUMPOD0=$(kubectl get -l k8s-app=cilium pods -n kube-system --field-selector spec.nodeName=k8s-ctr -o jsonpath='{.items[0].metadata.name}')
export CILIUMPOD1=$(kubectl get -l k8s-app=cilium pods -n kube-system --field-selector spec.nodeName=k8s-w1 -o jsonpath='{.items[0].metadata.name}')
export CILIUMPOD2=$(kubectl get -l k8s-app=cilium pods -n kube-system --field-selector spec.nodeName=k8s-w2 -o jsonpath='{.items[0].metadata.name}')
echo $CILIUMPOD0 $CILIUMPOD1 $CILIUMPOD2
## 단축키(alias) 지정
alias c0="kubectl exec -it $CILIUMPOD0 -n kube-system -c cilium-agent -- cilium"
alias c1="kubectl exec -it $CILIUMPOD1 -n kube-system -c cilium-agent -- cilium"
alias c2="kubectl exec -it $CILIUMPOD2 -n kube-system -c cilium-agent -- cilium"
##
c0 fqdn cache list
c1 fqdn cache list
c2 fqdn cache list
Endpoint Source FQDN TTL ExpirationTime IPs
363 connection support.github.com. 0 2025-08-31T05:10:05.726Z 185.199.111.133
363 connection support.github.com. 0 2025-08-31T05:10:05.726Z 185.199.108.133
363 connection api.github.com. 0 2025-08-31T05:10:05.726Z 20.200.245.245
c0 fqdn names
c1 fqdn names
c2 fqdn names
{
"DNSPollNames": null,
"FQDNPolicySelectors": [
{
"regexString": "^api[.]github[.]com[.]$",
"selectorString": "MatchName: api.github.com, MatchPattern: "
}
]
}
DNS Engress 정책 적용 2
kubectl delete cnp fqdn
kubectl apply -f https://raw.githubusercontent.com/cilium/cilium/1.18.1/examples/kubernetes-dns/dns-pattern.yaml
kubectl get cnp
kubectl exec mediabot -- curl -I -s https://support.github.com | head -1
kubectl exec mediabot -- curl -I -s https://gist.github.com | head -1
kubectl exec mediabot -- curl -I -s --max-time 5 https://github.com | head -1
kubectl exec mediabot -- curl -I -s --max-time 5 https://cilium.io| head -1
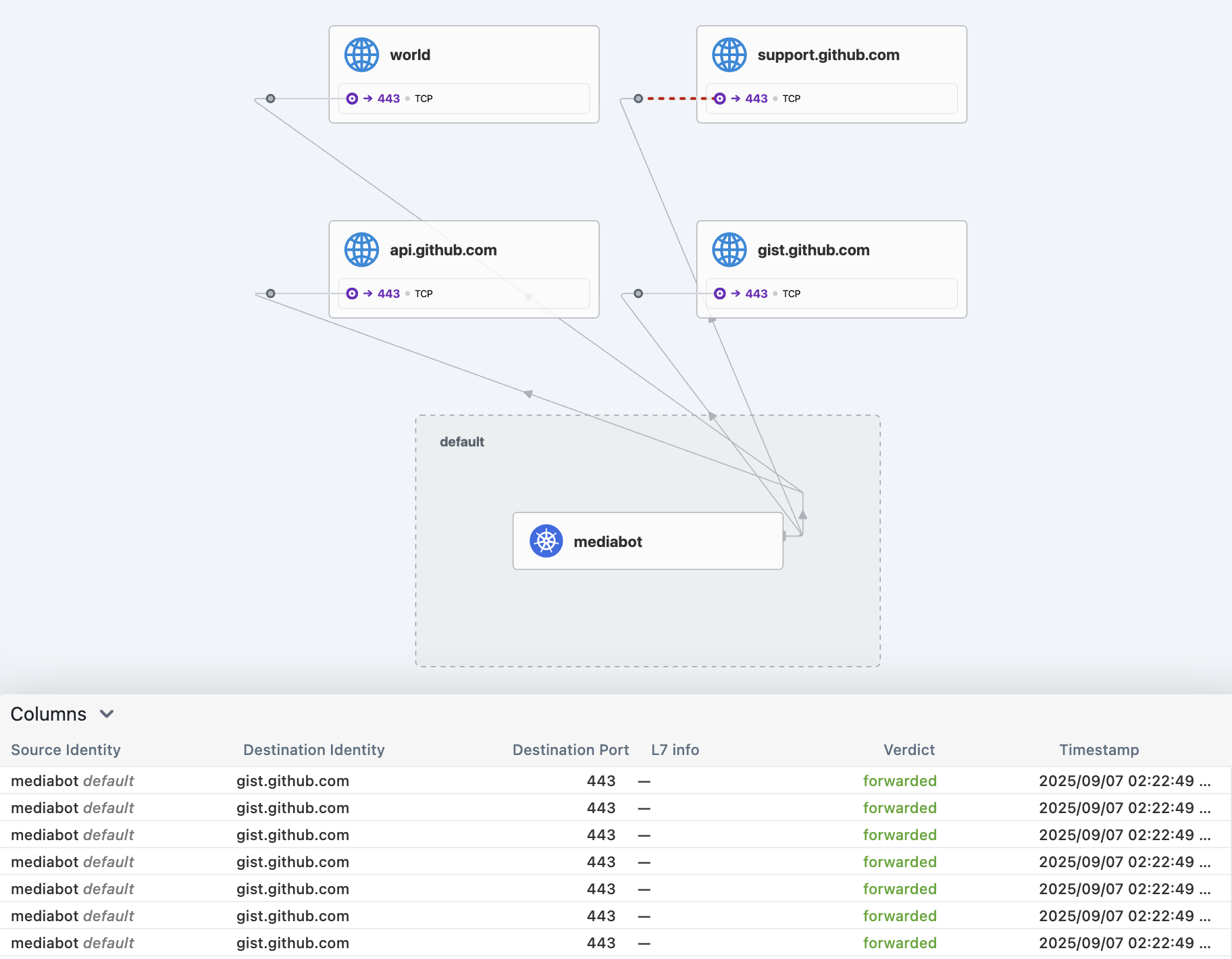
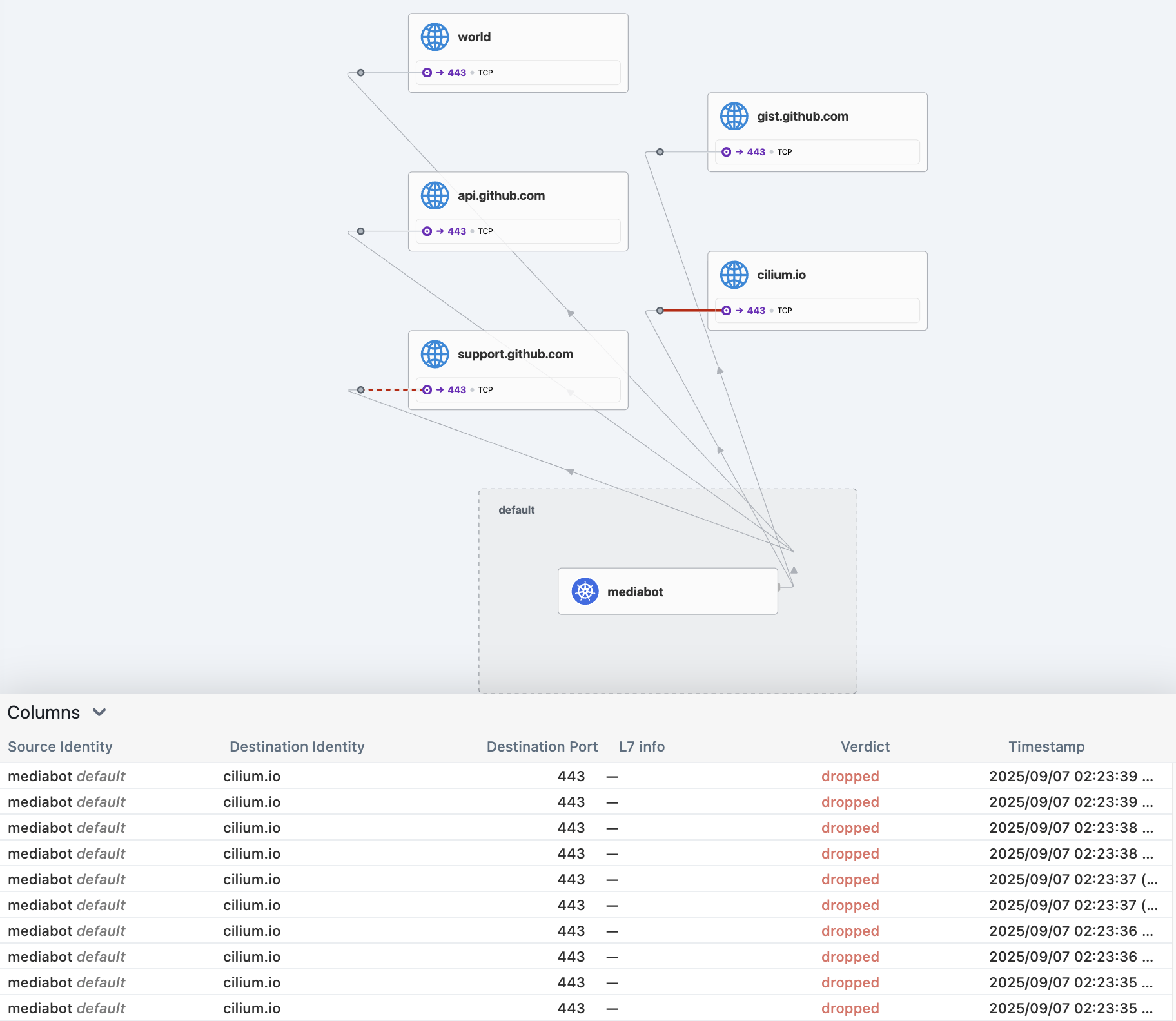
DNS Egress 정책 적용 3
kubectl apply -f https://raw.githubusercontent.com/cilium/cilium/1.18.1/examples/kubernetes-dns/dns-port.yaml
# 외부 통신 확인 : hubble ui 에서 확인
kubectl exec mediabot -- curl -I -s https://support.github.com | head -1
kubectl exec mediabot -- curl -I -s --max-time 5 http://support.github.com | head -1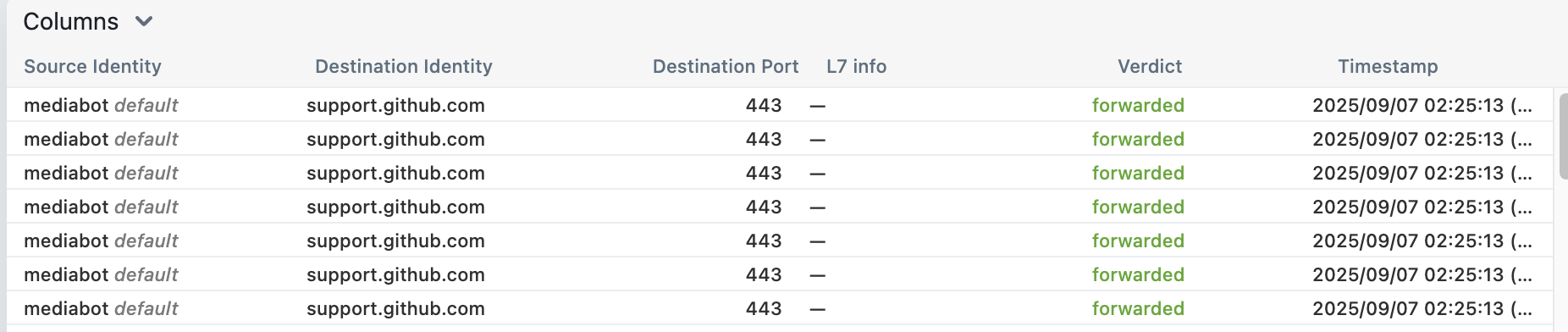
실습 리소스 삭제
kubectl delete -f https://raw.githubusercontent.com/cilium/cilium/1.18.1/examples/kubernetes-dns/dns-sw-app.yaml
kubectl delete cnp fqdn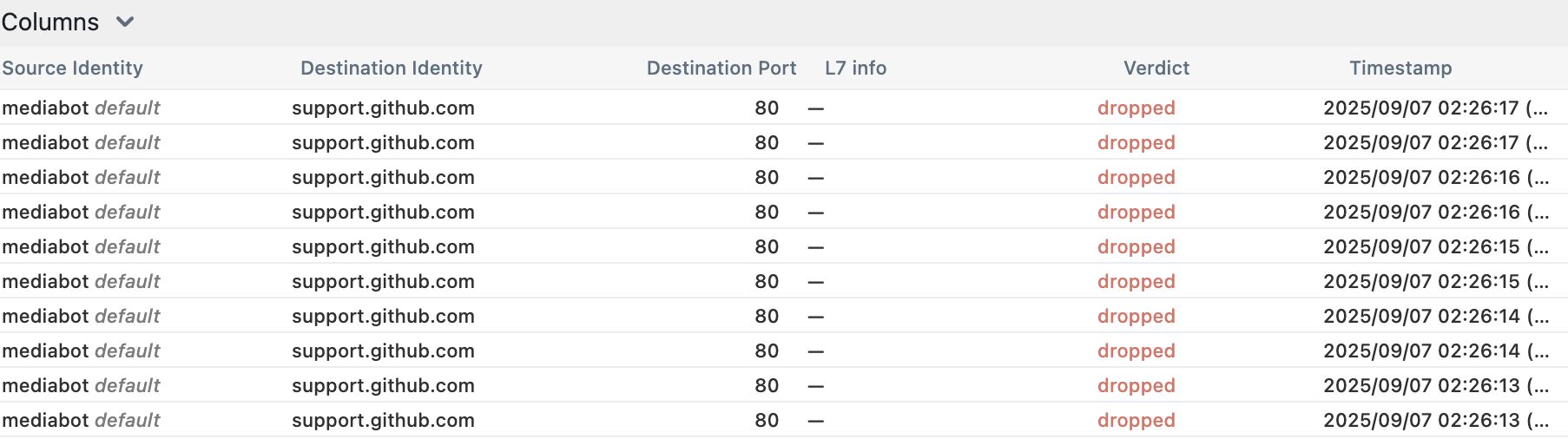
'DevOps > cilium' 카테고리의 다른 글
| [Cilium Study] Cilium Security (0) | 2025.09.07 |
|---|---|
| [Cilium Study] Cilium Performance (0) | 2025.08.31 |
| [Cilium Study] kube-burner (0) | 2025.08.30 |
| [Cilium Study] Mutual Authentication (0) | 2025.08.23 |
| [Cilium Study] Cilium Service Mesh 3 (0) | 2025.08.20 |